- WARNING: When replacing a mobile device, it is essential to first verify full MFA functionality with the new phone and only then delete the original device.
- None of my MFA verification methods are working – I cannot log in
- I lost my phone/security key
- I don’t have/don’t want to use a mobile device
- Other frequently asked questions
Available MFA Verification Options
| Microsoft Authenticator | Windows Hello | USB FIDO2 Key | TOTP | Temporary Access Pass (TAP) | |
| I use Windows | • | • | • | • | • |
| I use MacOS | • | • | • | • | |
| I use Linux | • | • | • | • | |
| I don’t have a smartphone | • | • | • | • |
MFA Authentication Methods at CTU
| Method | Description | Features | Requirements |
| Microsoft Authenticator (more) |
Mobile application for secure login to Microsoft accounts and other CTU services |
|
|
| Windows Hello (more) |
Verification uses Windows login |
|
|
| USB Fido2 Key (more) |
Security key that connects to computer via USB (or wirelessly via NFC) |
|
|
| TOTP Application (more) |
Third-party application that displays one-time numeric codes during login, changing every 30 seconds (for example Google authenticator) |
|
|
| Temporary Access Pass (TAP) | Code that user receives in person at CTU Card Center |
|
|
It is possible to have multiple authentication methods set up simultaneously.
Recommended Multi-Factor Authentication Setup
Microsoft Authenticator can be installed on Android 8+ and iOS16+ versions. Depending on the operating system version, individual steps when adding an account may vary.
Application icon:
1 |
On your phone, install the Microsoft Authenticator application: Android: Play Store / iPhone: App Store Make sure you install the correct application! (see icon above!) |
4 |
On your phone, launch the Microsoft Authenticator application and select Add account, or click + in the top right and choose Work or school account. Then select Scan QR code. |
2 |
On your computer, go to https://mysignins.microsoft.com/security-info and log in using your university account in the format username@cvut.cz and your CTU password. |
5 |
Point your phone at your computer screen and scan the QR code. This will add the CTU account to the application on your phone. On the computer screen, confirm Next. |
3 |
Click + Add sign-in method and select Microsoft Authenticator. In the wizard, choose Next twice in a row and then a unique QR code will be generated. |
6 |
A numeric code will appear on the computer screen, which you should enter into the application on your phone and confirm. After clicking the Next button, your CTU account is protected by MFA. |
After setting up the MFA application, we recommend activating the passwordless login feature, see detailed guide.
How Multi-Factor Verification Works in Microsoft Authenticator
 |
 |
 |
|
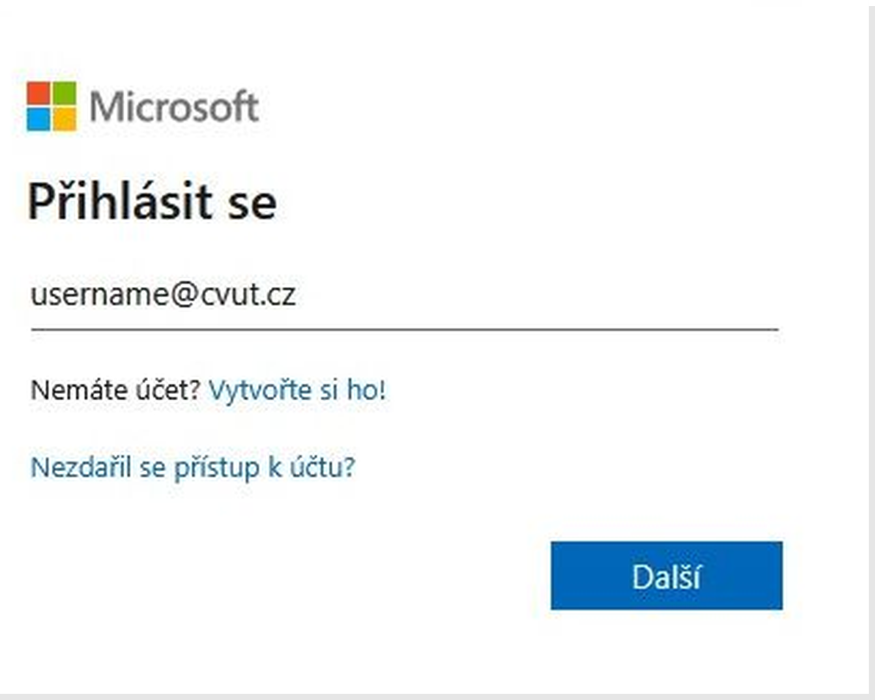
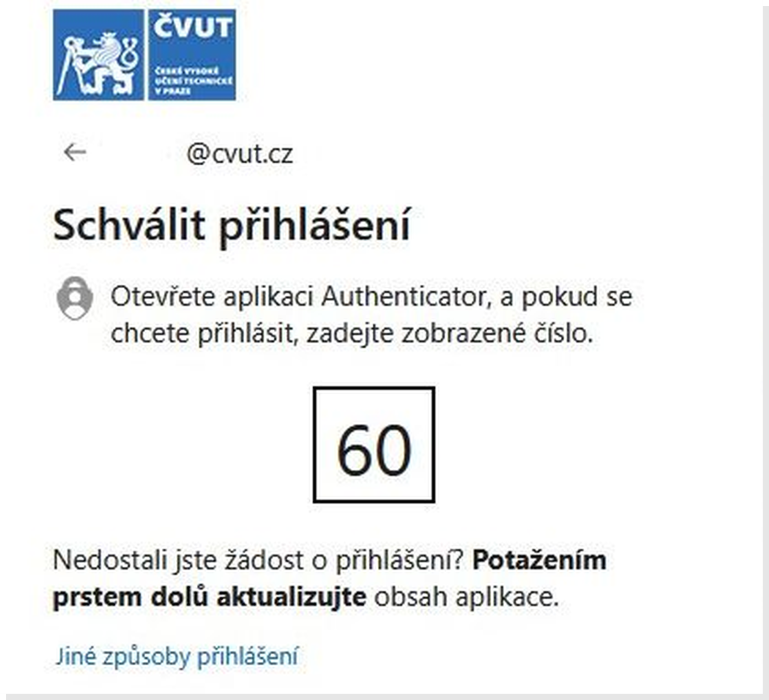
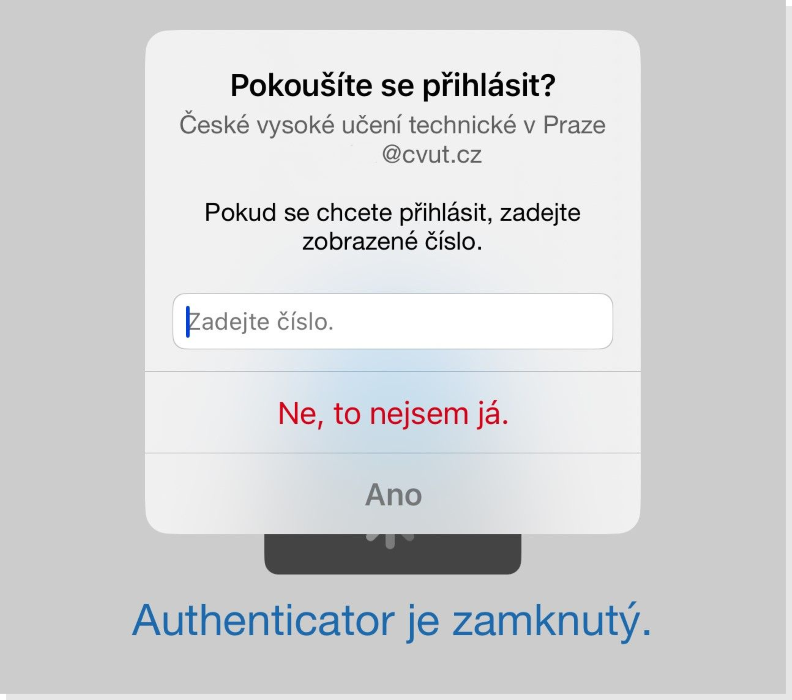
On computer: When accessing the service, enter your username. |
On computer: A unique numeric code will be displayed. |
On mobile device: Enter the code displayed on the computer into the application on your phone |
- Detailed information, procedures and additional settings can be found in the chapters below. In case of problems, contact faculty IT.
- FEE operates its own MFA login solution for its services, this solution is different from the University MFA!
The abbreviation MFA comes from the English term Multi-Factor Authentication, which in Czech means multi-factor verification or multi-factor authentication. It is a security mechanism that increases the level of user account protection by requiring identity verification using multiple independent methods.
We commonly encounter MFA, for example, when logging into internet banking. You may also encounter the term 2FA (two-factor verification or two-factor authentication), which designates a specific case of multi-factor verification using two different authentication elements.
How does MFA work?
Multi-factor verification adds another verification step to regular password entry, which serves to confirm the user’s identity. This second factor can take various forms – for example, a one-time code sent to a mobile phone, verification using a security key, or biometric verification (e.g., fingerprint).
MFA is typically based on a combination of the following types of credentials:
- Something you know – for example, a password or PIN code
- Something you have – a physical device, such as a mobile phone, hardware token – USB FIDO2 key
- Something you are – biometric data, such as fingerprint or facial recognition
Multi-factor authentication (MFA) represents an effective security measure that significantly strengthens the protection of user accounts, sensitive data and access to university systems. Its goal is to minimize the risk of unauthorized access, even if login credentials are compromised.
Unlike traditional login, which relies only on password knowledge, MFA requires an additional verification element – for example, a code sent to a mobile device, biometric verification, or use of a security key. Thanks to this, the account is protected even if an attacker gains access to the password – without the second factor, they cannot access sensitive information.
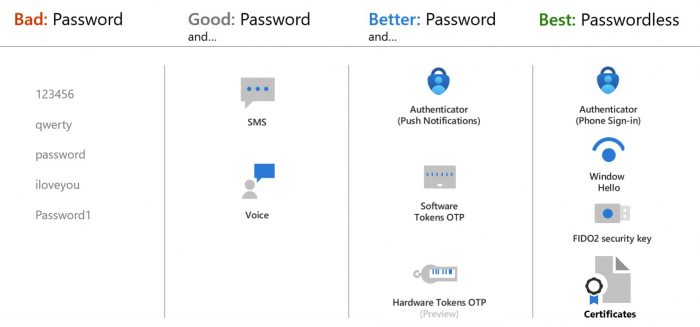
Based on experience with using multi-factor authentication (MFA) in the CTU environment, we recommend users utilize the following methods, which ensure maximum convenience and efficiency during verification.
 I use MS Windows:
I use MS Windows:
- We recommend using a mobile phone with the MS Authenticator application (guide)
- Activate the passwordless login feature in the MS Authenticator application, which enables more convenient and secure access without entering a password (guide)
- On computers with Windows operating system, we recommend enabling Windows Hello login, for example through fingerprint, facial recognition or PIN code (guide)
- We recommend connecting work or school computers to Microsoft Intune service, thereby ensuring device management and higher level of security. For personal devices, we recommend registering the device for MFA management (guide)
- In the web browser you use, enable single sign-on for Windows:
 I use MacOS:
I use MacOS:
- We recommend using a mobile phone with the MS Authenticator application (guide)
- Activate the passwordless login feature in the MS Authenticator application, which enables more convenient and secure access without entering a password (guide)
- We recommend connecting work or school computers to Microsoft Intune service, thereby ensuring device management and higher level of security. Personal devices cannot be connected to Intune!
- Then on the macOS computer, activate the Touch ID login option.
 I use Linux:
I use Linux:
- We recommend using a mobile phone with the MS Authenticator application (guide)
- Activate the passwordless login feature in the MS Authenticator application, which enables more convenient and secure access without entering a password (guide)
- Set up a backup MFA method (USB Fido2 key) (guide)
For trouble-free and secure use of MFA, we recommend registering at least two second factors. This prevents complications in case of loss or unavailability of one of them. For example, if you lose access to your mobile phone, you can still verify yourself using biometrics or a physical security token (USB FIDO2 key).
It is a mobile application that enhances the security of your accounts by serving for multi-factor authentication (MFA) – either by approving login via “approve/deny” notification on the phone, or by generating time-limited codes, thereby replacing or supplementing passwords and also enabling passwordless login using fingerprint, facial recognition or PIN.
- Push Notifications: Instead of entering codes, simply confirm login by tapping “Approve” in the application, which is faster and more secure.
- Time-based codes (TOTP): Generates six-digit codes that change every 30-60 seconds for an additional layer of security when notifications are not available.
- Passwordless login: Allows login without entering a password, only using biometrics (fingerprint, face) or device PIN.
- Passkey: Option to use passkey authentication.
- Support for various accounts: Can add personal Microsoft accounts (Outlook.com, OneDrive), work and school accounts.
What will you need?
- Mobile phone, (iOS 16+, Android 8+)
Installation and Configuration of the Application Using Computer and Phone
- On your phone, install the Microsoft Authenticator application (iOS 16+, Android 8+):
- Android: Google Play Store
- iPhone: App Store
- On your computer, open the website https://mysignins.microsoft.com/security-info.
- Log in using your university account in the format username@cvut.cz and password.
- Click +Add method, choose Microsoft Authenticator and continue until a QR code appears on the screen, which you scan on your phone.
- On your phone, launch the Microsoft Authenticator application.
- Select the + (plus) icon in the top right corner.
- Choose the option Work or school account, scan QR code and using your phone’s camera scan the QR code displayed on the computer screen.
- After successful scanning, the account is automatically added to the application.
- On the computer, complete the wizard for adding the application, which will prompt you to verify.
- If everything is set up correctly, a confirmation of successful addition of the Microsoft Authenticator application will appear on the computer.
Older versions of Android and iOS operating systems may not support all features or offer the same Microsoft Authenticator application setup options as newer devices. In some cases, individual setup steps may also differ.
Windows Hello for Business represents a secure and convenient login method that allows login without entering a traditional password. Instead, it uses biometric data (e.g., fingerprint or facial recognition) or PIN code, which ensures fast and secure login.
This method is designed with user comfort and high level of security in mind. Credentials are encrypted and stored locally directly in the device, never transferred to servers, which significantly increases privacy protection. Activation of Windows Hello for Business is required separately for each device.
What will you need?

- Windows 11
- Work/school account login (EntraID)
- You must have another MFA method activated (e.g., Microsoft Authenticator)
- If Microsoft Authenticator cannot be used, contact your faculty’s IT.
- TPM 2.0 chip (how do I check the version)
How to set up Windows Hello for Business:
- Open Settings: Start → Settings → Accounts → Sign-in options
- Select login method:
- Facial recognition
- Fingerprint
- PIN code
- Set up PIN (mandatory step): Enter and confirm your PIN. You can add letters and symbols to increase security.
- Setting up biometric data (optional step):
- Facial recognition
- Fingerprint
USB FIDO2 key is a small physical device (e.g., YubiKey, Token2) that serves for secure login without a password or as a second verification step.
Instead of copying codes, simply insert the key into a USB port (or tap via NFC) and confirm login with a touch or PIN. Login is fast, simple and very secure, because the key only works with specific websites and accounts and cannot be misused remotely.
USB Fido2 keys can also be used for passwordless login:
What will you need?
- USB Fido2 key (e.g., YubiKey, Token2)
- Computer with USB port and supported browser (latest versions: Edge, Chrome, Firefox, Safari)
- You must have another MFA method activated (e.g., Microsoft Authenticator)
- If Microsoft Authenticator cannot be used, contact your faculty’s IT.
Key registration:
- Log into your profile at: https://mysignins.microsoft.com/security-info
- Click +Add method, choose Security key and then USB or NFC.
- Insert the USB Fido2 key into the USB port and follow the displayed instructions.
- Set up touch verification or PIN and name your USB Fido2 key.
- After successful registration, the key will appear in the list of sign-in methods.
Login using USB Fido2 key:
- On the login screen, choose More sign-in options and select Security key.
- Insert the USB Fido2 key into the USB port and confirm verification.
Third-party application that displays one-time numeric codes during login, changing every 30 seconds (for example Google authenticator)
What will you need?
-
Mobile phone or computer with TOTP application (e.g., Google Authenticator, Authy, FreeOTP, KeePassXC)
TOTP registration:
- Log into your profile: https://mysignins.microsoft.com/security-info
- Click + Add method / Add method
- Choose Microsoft Authenticator application (this is the mandatory default step that the system requires)
- Choose another TOTP application
- After selecting Microsoft Authenticator, you will see the option „Use a different app” / Use a different authenticator app
- Select this option
- A QR code or secret key (secret / seed) will be displayed
Setting Up Third-Party Application
- Open the selected TOTP application on your phone
- Add new account:
- Scan the QR code, or
- Manually enter the secret key
- The application will start generating time-based codes (OTP), usually every 30 seconds
Completing Registration
- Enter into the web form the current code from the application to verify that everything works
- After confirmation, the method will appear in your list of sign-in methods
If you have purchased a new phone and want to use Microsoft Authenticator on it for logging into your work or school account, follow the Microsoft Authenticator setup steps, but additionally you will need to verify the application on the new phone using the application on the old phone.
When replacing a device, do not delete or factory reset the old phone until MFA is successfully set up on the new phone!
When using the data transfer function between phones, the MFA configuration does not transfer! MFA must be set up manually again on the new phone!
What to do if I don’t have the old phone?
- If you no longer have the old phone, log in using a previously set up backup method at https://mysignins.microsoft.com/security-info.
- If you do not have any backup method available, contact IT support, who will help you restore access.